CONCEPT DOMAIN - Operational Risk Assurance
| Description | The Operational Risk Assurance domain is the discipline of mastering operational risks. |
|---|---|
| Dictionary |  Dictionary of SysFEAT concepts
Dictionary of SysFEAT concepts |
| Parent Domain |  SysFEAT Enterprise Domains
SysFEAT Enterprise Domains |
| Domain dependencies |  Appraisal Pattern
Appraisal Pattern  Measurement
Measurement  Operational Assurance
Operational Assurance  Policies
Policies |
DOMAIN CONCEPT GRAPH
CONCEPT DESCRIPTIONS
ABSTRACT CONCRETE
| Concept | Description |
|---|---|
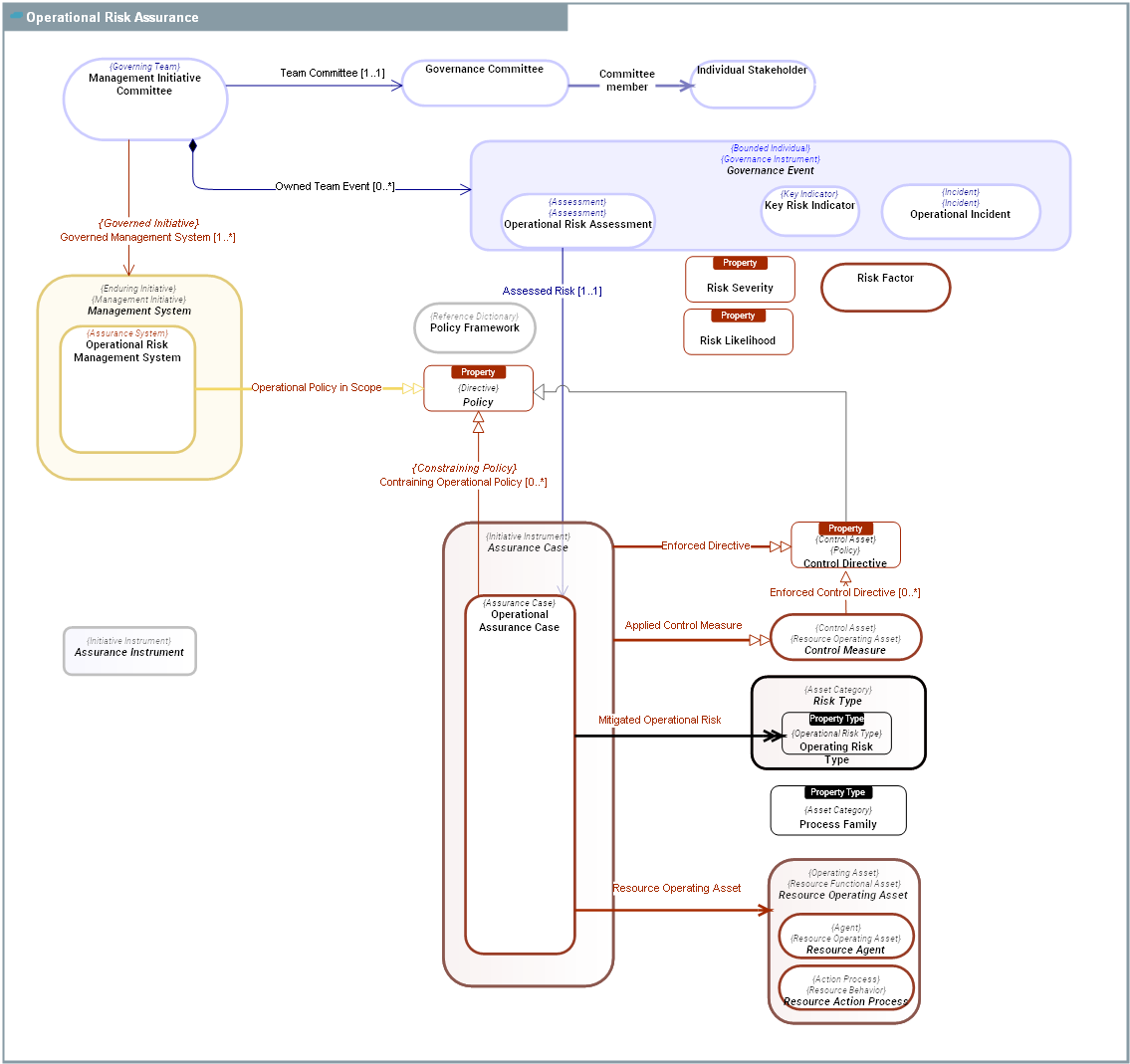
 Assurance Case
Assurance Case |
An Assurance Case is a claim that a particular enterprise asset or group of Functional Asset adequately mitigates certain identified Risk Types by means of appropriated Control Measures. An Assurance Case shall provide confidence that the concerned assets will function as intended in their environment of use. Privacy Processing Activity(ies), Data Lineages are examples of Assurance Cases .
|
 Assurance Instrument
Assurance Instrument |
An Assurance Instrument is a resource or course of actions used by an Assurance System to achieve its objectives. For instance: Actions plans are course of actions aimed at solving incidents. Data Controls are mechanisms used to ensure data quality and data integrity Privacy Representatives are used to identify national entities in charge of privacy. |
 Governance Event
Governance Event |
A Governance Event is any event that has an impact on the management and governance of an Enduring Initiative. |
 Management System
Management System |
A Management System is a mezzo Enduring Initiative within an Enterprise, aimed at creating, maintaining, evaluating, evolving, and operating a collection of essential Functional Architecture Assets of the Enterprise. A Management System may transcend organisational boundaries and consequently requires an integrated team working under the direction of a Management Initiative Committee.
|
 Policy
Policy |
A Policy is a Directive that is not directly enforceable whose purpose is to govern, guide or constrain the structure and Behavior Type of Agent Types in the enterprise. Policies provide the basis for rules and govern Behavior Types carried out by Agent Types.
|
 Policy Framework
Policy Framework |
A Policy Framework is a set of Policy Assets, defined in laws published by governements or in policy frameworks defined by the enterprise. Both Business Policy Frameworks and Regulatory Frameworks are Policy Framework(ies).
|
 Resource Action Process
Resource Action Process |
A Resource Action Process is a Action Process Type that describes a typical course of action intended to produce and react to Resource Outcome Events, through the involvement of Resource Agent Types (Participant Resource Agent). During its course of action, a Resource Action Process consumes or produces Resource Assets. 1) It may memorize or access Resource Assets to and from its Process Stores. 2) It may receive Resource Assets at its boundary: Resource Outcome Consumptions. 3) It may signal the production of Resource Assets at its boundary: Resource Outcome Productions. The course of actions of an Resource Action Process is constrained by the application of rules ( Resource Rule Enforcement) that define what is allowed and not allowed to do. Within SysFEAT, we can examine Resource Action Processes from two distinct perspectives: a) An operations business perspective is offered by Business Processes. c) An automated viewpoint is provided by System Processes.
|
 Resource Agent Type
Resource Agent Type |
A Resource Agent Type is an entity type which instance belongs to the physical space, and comprises Human Agent Categorys, Hardware System Categorys, Software System Categorys and Natural Resource Categorys. Resource Agent Type is the supertype of all types of Agent Types that produce and react to Resource Outcome Events. This includes: 1) Business Agent Types which represent physical resources that produce and react to Business Outcome Events of the enterprise. 2) Technology Systems which represents enabling systems that produce and react to Technology Outcome Events. |
 Resource Operating Asset
Resource Operating Asset |
Resource Operating Assets comprise all resources which contributes to the production and consumption of Business Outcome Events of the enterprise. Resource Operating Assets are subject to Operational Risks. |
 Risk Type
Risk Type |
A Risk Type is a distinct category or classification of risk based on its origin, nature, or potential impact. It helps in organizing and addressing different sources of uncertainty or potential harm that an individual, organization, or system might face. By categorizing risks into different types, entities can develop more targeted mitigation strategies and response plans. Common risk types include Operational Risk Type, Privacy Risk Type, and Compliance Risk Type, among others, |
SERIALIZATION FORMAT
TEXTUAL SYNTAX RDF
 NIST - Assurance Case
NIST - Assurance Case