CONCEPT DOMAIN - Operational Assurance
| Description | Pattern Domain The Operational Assurance domain provides a framework for systematic and evidence-based methodologies for ensuring that an enterprise's processes, systems, and services consistently meet defined trustworthiness criteria across multiple domains, including privacy, safety, security, business continuity, and quality. It establishes a structured framework for: 1) Trustworthiness - Ensuring that organizational operations demonstrably achieve acceptable levels of dependability, resilience, and compliance with regulatory and stakeholder expectations. 2) Risk-Informed Assurance - Aligning assurance initiatives with risk management to prioritize cost-effective controls while mitigating critical threats. 3) Continuous Validation - Employing monitoring, testing, audits, and performance metrics to verify that assurance objectives are sustainably met. 4) Cross-Domain Integration - Providing a unified approach to assurance that harmonizes domain-specific requirements (e.g., privacy, security, safety) while avoiding redundancy. 5) Stakeholder Confidence - Delivering transparent, auditable evidence to internal and external stakeholders that operational risks are managed effectively. As an overarching pattern, Operational Assurance enables coherent implementation of Privacy Assurance, Safety Assurance, Security Assurance, Business Continuity Planning, and Quality Assurance by standardizing governance, assessment methodologies, and accountability mechanisms. |
|---|---|
| Dictionary |  Dictionary of SysFEAT concepts
Dictionary of SysFEAT concepts |
| Parent Domain | |
| Domain dependencies |  Architecture Assets
Architecture Assets  Enterprise Architecting & Management
Enterprise Architecting & Management  Initiative and Transformation Pattern
Initiative and Transformation Pattern  Model Block Packaging
Model Block Packaging  People & Accountability
People & Accountability  Policies
Policies  Risk & Threat
Risk & Threat  SOF - Resource System Operating Pattern (R-SOF)
SOF - Resource System Operating Pattern (R-SOF)  System Operating Framework - SOF
System Operating Framework - SOF |
DOMAIN CONCEPT GRAPH
CONCEPT DESCRIPTIONS
ABSTRACT CONCRETE
| Concept | Description |
|---|---|
 Agent Type
Agent Type |
An Agent Type is an Operating Asset Type which is able to participate actively to Behavior Types, to produce and react to Outcome Events. 1. Agent Types participate to Action Process Typees (Active Participant) and/or conduct Action Process Typees (Performed Process). 2. Agent Types participate to Interaction Process Type (Scenario Participant) describing how they interact with other Agent Types. These actions and interactions define Agent Types boundaries described by Service Interfaces.
|
 Assurance Case
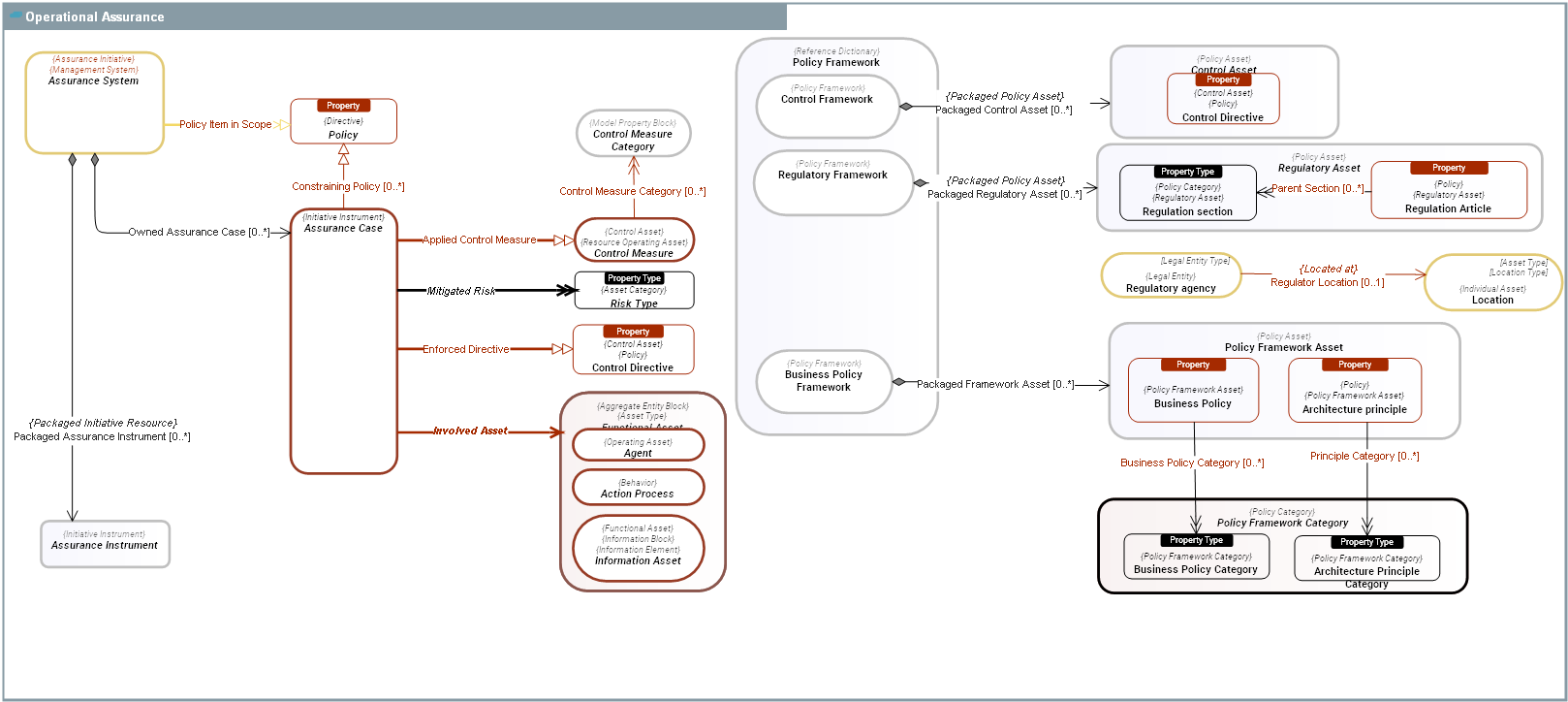
Assurance Case |
An Assurance Case is a claim that a particular enterprise asset or group of Functional Asset adequately mitigates certain identified Risk Types by means of appropriated Control Measures. An Assurance Case shall provide confidence that the concerned assets will function as intended in their environment of use. Privacy Processing Activity(ies), Data Lineages are examples of Assurance Cases .
|
 Assurance Instrument
Assurance Instrument |
An Assurance Instrument is a resource or course of actions used by an Assurance System to achieve its objectives. For instance: Actions plans are course of actions aimed at solving incidents. Data Controls are mechanisms used to ensure data quality and data integrity Privacy Representatives are used to identify national entities in charge of privacy. |
 Assurance System
Assurance System |
An Assurance System is a Management System aimed at ensuring enterprise compliance, resilience, and risk mitigation against both internal and external Policys and threats. It encompasses processes, Directives and technologies that work in concert to validate enterprise adherence to policy requirements, industry standards, and internal policies while simultaneously bolstering the enterprise's ability to withstand and adapt to various challenges and disruptions. ensuring enterprise compliance and resilience against internal and external constraints: a. Regulation constraints: they defined what is allowed and not allowed by the law (See Regulation Article). b. Internal policies and rules constraints: they defined what is allowed and not allowed by the enterprise (see Business Policy). c. Operational constraints: they maintain operational capacities of the company (maintain ability to produce, maintain quality, ensure product development , ability to hire, to train, etc, see Business Rule). d. Architectural constraints: they guide design decisions and shape the overall structure of a system (see Architecture principle). |
 Behavior Type
Behavior Type |
A Behavior Type is an Operating Asset Type that describes any action or reaction of an Agent Type to external or internal Behavioral Events. Behavior Types include Action Process Typees (action), Interaction Process Types (stories) or interactions (Service Interface). The course of actions of a Behavior Type is constrained ( Rule Enforcement) by the application of Behavioral Rules that define what is allowed and not allowed to do.
|
 Control Asset
Control Asset |
A Control Asset is a Policy Asset that is part of a Control Framework. |
 Functional Asset
Functional Asset |
Functional Assets encompasse all Asset Types used to describe why and how systems operate/function. This includes the Operating Eco-System where system operates to fulfill these purposes (Agent Types and their Behavior Types). Functional Assets include: 1. Blocks defining results of Behavior Types of the enterprise or its sub-systems, that benefit to it internal or external customers : Outcome Event, 2. Blocks used to describe information: Information Asset. 3. Blocks used to describe how the enterprise operates: Operating Asset Types (Agent Type, Behavior Type, Service Interface).
|
 Information Asset
Information Asset |
An Information Asset represents anything that can be communicated or memorized by an Agent Type to produce and react to Outcome Events. An Information Asset is either an Information Entity or an Information Property.
The difference lies in their relationship to change and to time. Information Entity(ies) can change over time and have a lifeycle while Information Propertys are immutable characteristics. |
 Policy
Policy |
A Policy is a Directive that is not directly enforceable whose purpose is to govern, guide or constrain the structure and Behavior Type of Agent Types in the enterprise. Policies provide the basis for rules and govern Behavior Types carried out by Agent Types.
|
 Policy Framework
Policy Framework |
A Policy Framework is a set of Policy Assets, defined in laws published by governements or in policy frameworks defined by the enterprise. Both Business Policy Frameworks and Regulatory Frameworks are Policy Framework(ies).
|
 Policy Framework Asset
Policy Framework Asset |
A Policy Framework Asset is a Policy Asset that is declared in a Business Policy Framework. |
 Policy Framework Category
Policy Framework Category |
Policy Framework Category is a place holder for Policy Category(ies) that are managed (owned by) in a Policy Framework. |
 Regulatory Asset
Regulatory Asset |
A Regulatory Asset is a Policy Asset that is part of of a Regulatory Framework. |
 Risk Type
Risk Type |
A Risk Type is a distinct category or classification of risk based on its origin, nature, or potential impact. It helps in organizing and addressing different sources of uncertainty or potential harm that an individual, organization, or system might face. By categorizing risks into different types, entities can develop more targeted mitigation strategies and response plans. Common risk types include Operational Risk Type, Privacy Risk Type, and Compliance Risk Type, among others, |
SERIALIZATION FORMAT
TEXTUAL SYNTAX RDF
 Christensen Institute - Modularity
Christensen Institute - Modularity