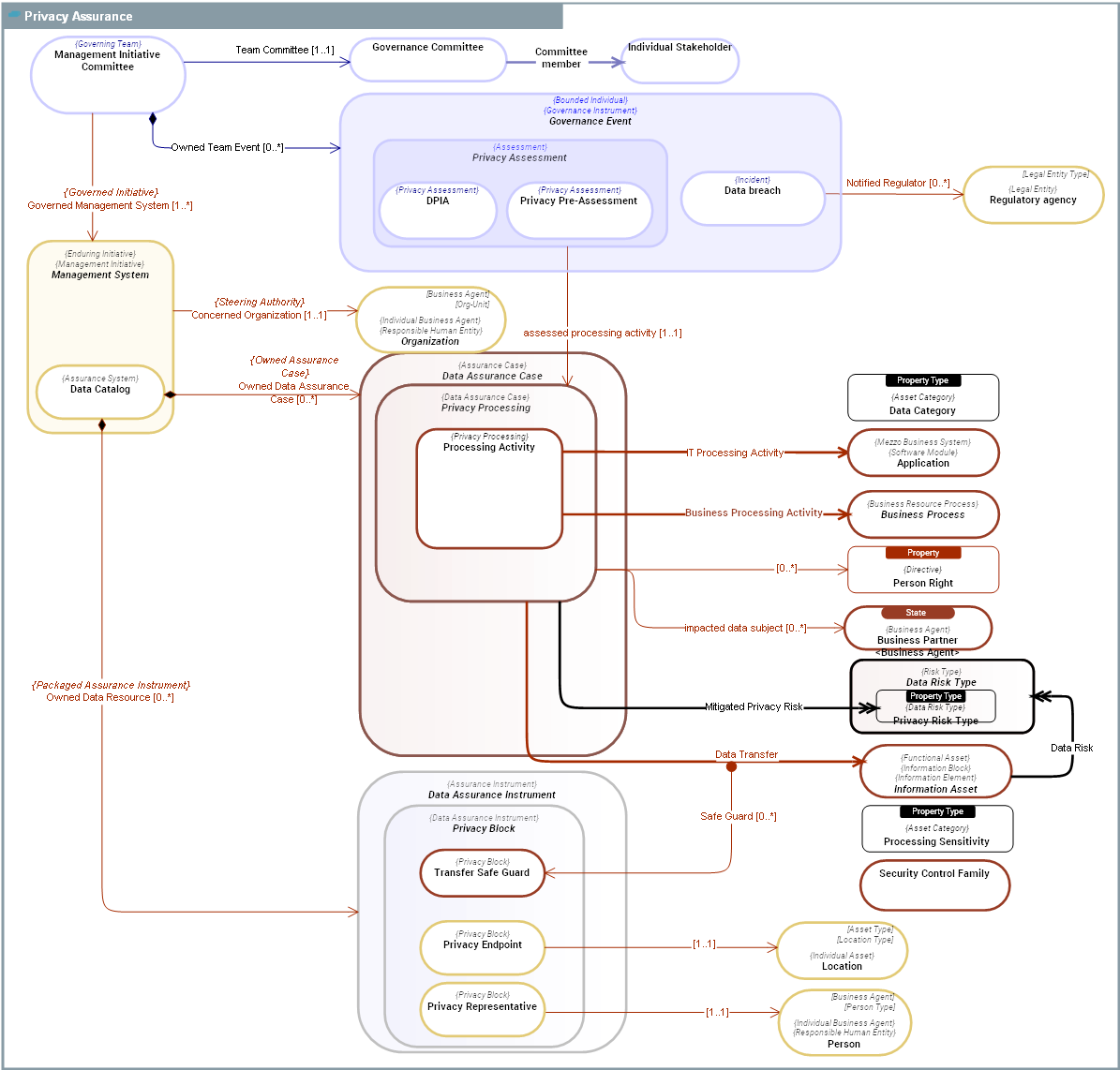
CONCEPT DOMAIN - Privacy Assurance
| Description | Privacy assurance offers strategies and schemes adopted by an organization to prevent the flow of important information outside of the workplace. The approach includes investigation, remediation and reporting. |
|---|---|
| Dictionary |  Dictionary of SysFEAT concepts
Dictionary of SysFEAT concepts |
| Parent Domain |  Data Governance
Data Governance |
| Domain dependencies |  Appraisal Pattern
Appraisal Pattern  Architecture Assets
Architecture Assets  Data Governance Core
Data Governance Core  Information Assets
Information Assets  Operational Assurance
Operational Assurance  People & Accountability
People & Accountability  Policies
Policies  Product & Customer Experience
Product & Customer Experience |
DOMAIN CONCEPT GRAPH
CONCEPT DESCRIPTIONS
ABSTRACT CONCRETE
| Concept | Description |
|---|---|
 Business Partner
Business Partner |
A Business Partner is a state of a Resource Agent Type, who acts as a party interacting with the enterprise in the context its operating eco-system (the Resource Operating Ecosystem). Example : Private Sector Customer, Regulation Authority, Public health Authority. |
 Business Process
Business Process |
A Business Process is a set of Business-Process Steps performed by Org-Unit Types and/or by automated systems (Business Systems) to produce a Business Outcome Event. It is depicted as a series of Business-Process Steps, controlled by Business Events and conditions. Business-Process Steps are carried out by the involvment of Org-Unit Types and system resources (often Applications) as participants in the process (Participant Business Agents). During its course of action, a Business Process consumes or produces Business Objects. 1) It may memorize or access Business Objects from its Process Store. 2) It may receive Business Objects at its boundary: Business Outcome Consumption. 3) It may signal the production of Business Objects at its boundary: Business Outcome Production. The course of actions of a Business Process is constrained by the application of rules ( Business Rule Enforcement) that define how to react to what is allowed and not allowed to do,
|
 Data Assurance Case
Data Assurance Case |
A Data Assurance Case is a structured argument, supported by evidence, intended to justify that a data is acceptably assured relative to a concern (such as quality, safety, security or privacy) in the intended operating environment. The operating environment includes: 1. Policies related to the use of data in the organization (privacy policy, regulation policy, ...). 2. Data quality policies defined by the organization. 3. Risk to be mitigated in the use, consumption and sharing of data by the organization. 4. Control directives to be followed in the use, consumption and sharing of data by the organization.
|
 Data Assurance Instrument
Data Assurance Instrument |
A Data Assurance Instrument is a resource or course of actions used by an Data Catalog to achieve its objectives. For instance: Actions plans are course of actions aimed at solving Data breaches. Data Controls are mechanisms used to ensure data quality and data integrity Data Processors are used to processings involved in Data Lineages. |
 Data Risk Type
Data Risk Type |
A Data Risk Type is a Risk Type that refers to the accuracy, consistency, and reliability of data during its entire lifecycle. |
 Governance Event
Governance Event |
A Governance Event is any event that has an impact on the management and governance of an Enduring Initiative. |
 Information Asset
Information Asset |
An Information Asset represents anything that can be communicated or memorized by an Agent Type to produce and react to Outcome Events. An Information Asset is either an Information Entity or an Information Property.
The difference lies in their relationship to change and to time. Information Entity(ies) can change over time and have a lifeycle while Information Propertys are immutable characteristics. |
 Management System
Management System |
A Management System is a mezzo Enduring Initiative within an Enterprise, aimed at creating, maintaining, evaluating, evolving, and operating a collection of essential Functional Architecture Assets of the Enterprise. A Management System may transcend organisational boundaries and consequently requires an integrated team working under the direction of a Management Initiative Committee.
|
 Organization
Organization |
An Organization is a group of people who share a common purpose and establish a functional division of labor in pursuit of their common purpose. It is the relationships between its members in the pursuit of their common purpose that give unity and identity to an organization.
|
 Person
Person |
A Person represents a human being that is recognized by law as the subject of rights and duties. |
 Privacy Assessment
Privacy Assessment |
|
 Privacy Block
Privacy Block |
|
 Privacy Processing
Privacy Processing |
A Privacy Processing is a Data Assurance Case related to any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organisation, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction |
SERIALIZATION FORMAT
TEXTUAL SYNTAX RDF
 ISO 9000 - 3.4.1 - Process
ISO 9000 - 3.4.1 - Process Martin Fowler - Application Boundary
Martin Fowler - Application Boundary